Business
Cracking the Code: The Mystery of 7473223727

Introduction
Imagine a world where numbers hold secrets waiting to be unraveled. Have you ever pondered the mysteries hidden within a simple string of digits, like 7473223727? The journey of cracking codes and understanding their significance can be thrilling and intellectually stimulating. This article explores the challenges and potential methods of cracking the code 7473223727.
We’ll dive into the historical context, mathematical properties, encryption complexities, techniques used for code cracking, famous case studies, and ethical considerations. Join me as we embark on this fascinating exploration.
Understanding the Number 7473223727
Historical Significance
The number 7473223727 may seem like a random sequence, but it can carry significant weight in various contexts. In the realm of codes and ciphers, seemingly random numbers often represent more than meets the eye. They may refer to historical events, popular culture references, or even encoded information within complex systems.
Exploring the potential historical significance of 7473223727 can lead us down various paths, from encryption in wartime communications to modern applications in technology and security.
Mathematical Properties
Examining the mathematical properties of 7473223727 can reveal fascinating insights:
- Prime Factorization: Unlike simple numbers, 7473223727 is a composite number, meaning it can be broken down into smaller prime numbers. Understanding its prime factorization helps in cryptographic applications.
- Divisibility Rules: The number can be analyzed for divisibility by various integers, which may have implications in specific encoding schemes.
Potential Origins
The origins of 7473223727 can vary widely. It could stem from:
- Encryption Algorithms: It might be part of a more extensive encryption algorithm, serving as a key or a hash in data security.
- Random Number Generators: It may have originated from random number generation processes used in statistical sampling or simulations.
Understanding where this number comes from can help in determining its relevance in specific contexts.
The Challenges of Code Cracking
Complexity of Encryption Algorithms
The world of cryptography is complex, filled with various encryption algorithms designed to protect sensitive information. These include:
- Symmetric Encryption: This method uses the same key for both encryption and decryption, making it faster but requiring secure key exchange.
- Asymmetric Encryption: This method employs a pair of keys—one public and one private—allowing for secure communications without the need to share private keys.
Each type of encryption poses unique challenges when attempting to crack the code 7473223727.
Computational Power Requirements
In our digital age, the computational power required to crack modern codes is immense. The process of code cracking often involves:
- High-Performance Computing: Successful cracking attempts typically rely on advanced computing resources, which may be out of reach for individual hackers.
- Distributed Computing: Many modern code cracking efforts harness the power of distributed networks to pool resources and increase efficiency.
Quantum Computing Threat
As technology evolves, so does the potential for quantum computing to revolutionize code cracking. Unlike classical computers, quantum computers use quantum bits (qubits), allowing them to perform calculations at speeds unimaginable with current technology. This advancement could render many traditional encryption methods obsolete, posing a significant threat to the integrity of coded information like 7473223727.
Code Cracking Techniques
Brute Force Attack
One of the most straightforward yet resource-intensive methods of code cracking is the brute force attack. This technique involves:
- Systematic Guessing: Attempting every possible combination of characters or digits until the correct one is found.
- Limitations: While brute force can be effective against simpler codes, the time required increases exponentially with the complexity of the code.
Frequency Analysis
Frequency analysis is a powerful tool in code cracking, particularly with substitution ciphers. It involves:
- Identifying Patterns: Analyzing the frequency of letters or numbers to identify common patterns and make educated guesses about the code.
- Application: This technique can be highly effective against codes like 7473223727 if they exhibit recognizable patterns.
Social Engineering
In addition to technical skills, code cracking often involves social engineering techniques. This method includes:
- Manipulating Individuals: Gaining information through interpersonal skills and psychology to discover secrets about the code or its origin.
- Phishing and Pretexting: Using deceitful tactics to obtain sensitive information from targets.
Advanced Cryptographic Attacks
More sophisticated attacks like differential cryptanalysis and linear cryptanalysis involve deep mathematical principles. These techniques can exploit weaknesses in specific encryption algorithms and are used primarily by professionals in the field.
Case Studies of Famous Code Cracking Attempts
Enigma Machine
One of the most famous instances of code cracking occurred during World War II with the breaking of the Enigma code. The efforts of mathematicians and cryptographers, most notably Alan Turing, led to significant advances in codebreaking, saving countless lives and altering the course of the war.
RSA Challenge
The RSA Factoring Challenge is another pivotal moment in the history of code cracking. The challenge involved factoring large numbers, pushing the limits of computational capabilities and testing the security of RSA encryption. Successful solutions have had profound implications for cryptography and data security.
Recent High-Profile Hacks
Recent examples of successful or unsuccessful code cracking attempts, such as the Yahoo! data breach and the WannaCry ransomware attack, highlight the importance of robust security measures in protecting sensitive information.
Ethical Considerations and Implications
Privacy and Security Concerns
As the landscape of code cracking evolves, ethical implications become increasingly prominent. The balance between security and privacy raises questions about the extent to which individuals’ data should be protected from unauthorized access.
Legal Issues
The legal aspects of code cracking can be complex. Intellectual property laws and copyright issues may arise, particularly when cracking codes for unauthorized purposes.
The Future of Cryptography
Looking forward, advancements in cryptography will continue to evolve, making it even more challenging to crack codes like 7473223727. Innovations in quantum-resistant algorithms and secure key exchange methods will play critical roles in shaping the future of digital security.
YOU MAY ALSO LIKE
8442955938 – A Toll-Free Number for Seamless Customer Support
Conclusion
In summary, understanding and cracking the code 7473223727 encompasses a myriad of historical, mathematical, and ethical dimensions. As technology advances, the complexities of encryption and code cracking will continue to evolve, highlighting the necessity for robust cryptographic practices.
As you explore this intriguing topic further, consider the importance of cryptographic security in our increasingly digital world.
FAQs
- What does the number 7473223727 represent?
- The number 7473223727 can have various meanings, potentially relating to historical events or encryption methods. Its significance depends on the context in which it is used.
- What are the main challenges of code cracking?
- Key challenges include the complexity of encryption algorithms, the need for substantial computational power, and the potential threat posed by quantum computing.
- What is a brute force attack in code cracking?
- A brute force attack involves systematically trying all possible combinations of a code until the correct one is found. It can be time-consuming and resource-intensive.
- How does frequency analysis aid in cracking codes?
- Frequency analysis identifies patterns in the use of characters or numbers, helping to make educated guesses about the encryption method used.
- What are some ethical concerns related to code cracking?
- Ethical concerns include privacy violations, the legality of cracking codes for unauthorized access, and the balance between security and individual rights.
Business
How to Apply Machine Stretch Film
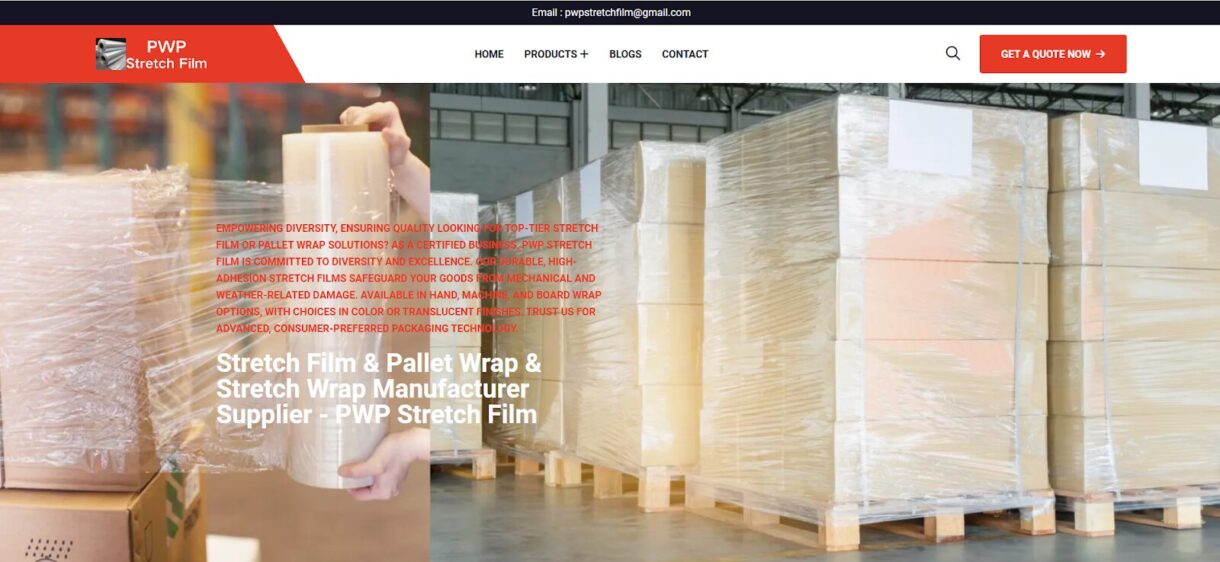
comprehensive guide
Machine stretch film is designed for automated packaging systems, where efficiency, consistency, and load security are essential. Properly applying machine stretch film to pallets or products is critical to ensure product integrity during transport and storage. The process requires both the right machine setup and knowledge of the film’s properties to achieve the best results. Machine stretch film is typically manufactured by leading producers such as PWP Stretch Film, who provide high-quality films tailored to meet the specific needs of automated packaging. Below is a comprehensive guide to applying machine stretch film effectively, covering key considerations for setup, application, and optimization.
Set Up the Stretch Wrapping Machine
- Check Film Compatibility: Before applying any type of stretch film, ensure the film type is compatible with your wrapping machine. Machine stretch film is generally designed for automated systems, while hand stretch film is typically used for manual wrapping applications.. Different machines may have specific requirements for the type of stretch film used, such as width, gauge, and roll core size. Ensure that the film roll is correctly loaded onto the machine, and that the film is positioned for smooth application.
- Adjust Machine Settings: One of the most crucial steps in applying machine stretch film is to adjust the machine’s settings. This includes controlling:
- Tension: The tension should be adjusted based on the type of film and the load being wrapped. Too much tension can cause the film to snap, while too little can result in weak wraps. Most stretch wrapping machines allow you to adjust the tension to achieve optimal stretch and load security.
- Pre-Stretch: Some machines come with pre-stretch capability, which allows the film to be stretched before it’s applied to the load. This helps to save material while still providing strong load containment. Adjust the pre-stretch settings according to the desired stretch ratio (e.g., 200%, 250%).
- Wrap Speed: Depending on your production environment and volume, adjust the wrap speed. Faster wrapping speeds improve throughput but may lead to uneven wraps, while slower speeds offer better precision but can decrease productivity.
Properly Load the Pallet or Product
- Evenly Distribute the Load: Ensure the products or materials on the pallet are evenly distributed. An uneven load can cause instability during wrapping, leading to poor film application. It’s important that the pallet is properly centered on the wrapping machine for consistent and even wraps.
- Ensure Stability: Check that the load is stable and properly aligned. Any shifting or tilting can result in gaps or tears in the film during the wrapping process. Some machines have adjustable features that help secure the load during the wrapping cycle.
Wrapping the Pallet
- Start from the Base: Begin the wrapping process at the base of the pallet and work your way up. This helps secure the bottom of the load first, ensuring stability. Many machines automatically start wrapping from the bottom and move upward, while others allow manual adjustment.
- Overlapping Layers: As the film is applied, make sure there is an adequate overlap between each layer. The amount of overlap will depend on the machine settings and the stretch film gauge. A typical overlap is around 50-70% of the film’s width. This ensures the film adheres securely to the load and provides greater stability during transport.
- Maintain Consistent Tension: While wrapping, it’s important to keep the film under consistent tension. The film should be applied with just enough stretch to secure the load, but not so much that it tears. Adjust the tension controls on the machine to maintain consistency across all layers.
- Top Layer and Edge Sealing: Once the pallet is wrapped, the top layer should be applied to seal the load and prevent the film from unrolling. Many stretch wrapping machines have the ability to automatically cut and seal the film at the top to secure the end of the wrap. Make sure that the edges are sealed tightly to prevent the film from loosening during transport.
Optimize Film Usage
- Use the Right Film Gauge: Choosing the right thickness or gauge of film is essential for efficient and cost-effective wrapping. Thicker films offer greater puncture resistance and load stability, but they are also more expensive. Lighter gauges are more cost-effective but may not provide the same level of strength. Selecting the right film gauge for your specific load type and weight helps minimize material waste and optimize performance.
- Adjust Pre-Stretch for Material Efficiency: Pre-stretching the film can significantly reduce material waste. By stretching the film before it is applied, you use less material while still achieving the same load security. Adjust the machine’s pre-stretch setting to find the optimal stretch ratio that works for your products.
- Monitor Film Waste: Monitor the amount of stretch film being used per unit and adjust the machine settings if necessary. Excessive use of film can be a sign of improper tension, incorrect pre-stretch, or poor machine calibration. Regularly check for any inconsistencies or waste in the wrapping process.
Safety Considerations
- Operator Safety: Machine stretch film application involves high-speed machinery, and safety is critical. Ensure that operators are trained in the safe operation of the stretch wrapping machine, including proper loading techniques, adjusting settings, and handling any issues that may arise during the wrapping process.
- Machine Safety Features: Many modern wrapping machines come with built-in safety features, such as emergency stop buttons, automatic film cutting, and sensors to prevent injury. Ensure that these features are in place and functioning properly.
- Personal Protective Equipment (PPE): Operators should wear appropriate PPE, including gloves and safety shoes, to protect against sharp edges and other hazards associated with handling stretch film and operating heavy machinery.
Maintenance of the Stretch Wrapping Machine
- Regular Cleaning: Dust, debris, and spilled film can accumulate on the machine and affect its performance. Regular cleaning of the machine ensures that it operates smoothly and reduces the risk of film jamming or uneven application. Pay special attention to rollers, film dispensers, and sensors.
- Routine Inspections: Periodically inspect the stretch wrapping machine for wear and tear, particularly on parts that interact with the film, like rollers and tensioners. Ensure that the machine is working correctly, especially when using more specialized films like VCI stretch film, which require careful handling to preserve its protective properties.
- Film Roll Replacement: Monitor the usage of film rolls and replace them when necessary. If the machine starts to struggle with applying the film correctly or if the film becomes damaged, it may be time to load a new roll. Ensure that the film is properly threaded and positioned before starting a new wrapping cycle.
Business
Retaliation in the Workplace: Identifying and Addressing Employer Misconduct

Retaliation in the workplace is a serious concern that can affect anyone. Understanding what constitutes employer misconduct is key to addressing it effectively. Retaliation occurs when an employer punishes an employee for engaging in a legally protected activity. These activities might include reporting harassment or discrimination, participating in an investigation, or refusing to engage in illegal actions. Recognizing retaliation involves spotting subtle signs like unjustified negative performance reviews, denial of promotions, or exclusion from important meetings. It’s important to address these issues promptly. Speaking up can seem daunting, but it protects your rights and promotes a healthier work environment. Legal experts, such as Sattiraju & Tharney, LLP, can provide guidance on navigating these complex situations. Many employees fear retaliation for voicing concerns, but understanding your rights can empower you. Remember, every step taken towards identifying and addressing employer misconduct contributes to a fairer workplace for all.
Understanding Employer Retaliation
Employer retaliation can manifest in various forms. It is crucial to differentiate between normal managerial actions and retaliatory behaviors. Retaliation might include:
- Sudden changes in job responsibilities
- Increased scrutiny or micromanagement
- Unwarranted disciplinary actions
These actions can create a hostile work environment, affecting morale and productivity. According to the U.S. Equal Employment Opportunity Commission, retaliation claims have consistently been the most frequently filed charges in recent years. This underscores the need for awareness and proactive measures.
Identifying Signs of Retaliation
Spotting retaliation requires vigilance. Employees should note any unusual changes in their work situation, especially following complaints or whistleblower activities. Key indicators include:
- Isolation from colleagues or team activities
- Unanticipated job transfers to less desirable positions
- Reduction in work hours or responsibilities
When these signs appear, it’s important to document everything. Keeping a detailed record of incidents, dates, and conversations can be crucial in building a case against retaliation.
Legal Protections Against Retaliation
Employees have legal protection under various laws. The Occupational Safety and Health Administration (OSHA) protects workers who report safety violations. Additionally, Title VII of the Civil Rights Act and the Americans with Disabilities Act include provisions against workplace retaliation.
These laws aim to ensure a safe reporting environment. Employees should familiarize themselves with these protections to better understand their rights and options.
Steps to Address Retaliation
If you suspect retaliation, taking the right steps is crucial. Here’s a simple approach:
- Document every instance meticulously. This includes keeping emails, memos, and any evidence of retaliatory behavior.
- Communicate concerns to a supervisor or HR. Sometimes, an open conversation can resolve misunderstandings or miscommunications.
- Seek legal advice if necessary. Lawyers specializing in employment law can provide insights and help you navigate the complexities of retaliation claims.
Comparison of Common Retaliation Examples
| Retaliation Example | Description | Impact |
| Negative Performance Review | Unjustly low performance ratings following a complaint | Can affect promotions and salary increments |
| Demotion or Pay Cut | Reduction in job position or salary without valid reason | Financial impact and job dissatisfaction |
| Exclusion from Meetings | Omitting an employee from important meetings | Leads to missed opportunities and isolation |
Conclusion
Addressing workplace retaliation is not only about protecting individual rights but also cultivating a culture of fairness. Awareness and education are the first steps in prevention. Encouraging open dialogue and understanding legal protections can help employees feel safe and valued. Taking action against misconduct helps foster a workplace where everyone has the opportunity to thrive without fear. By staying informed and proactive, we can all contribute to a more equitable work environment.
Business
The Importance of Timely Action in Post-Judgment Collections

In the world of post-judgment collections, timely action is crucial. Once a judgment is obtained, the window for effective recovery begins to close. Delays can lead to diminished returns and increased complications. Taking swift steps ensures the judgment remains enforceable and maximizes the chances of full collection. Warner & Scheuerman, known for their expertise in this area, highlight the significance of acting without hesitation. They emphasize that the faster you act, the better the outcome. Timing impacts the ease of locating debtor assets and navigating the legal maze. By acting promptly, one can avoid unnecessary hurdles and expenses. Furthermore, understanding the complexities of the collection process can make a significant difference. It’s about knowing when and how to pursue the next steps, ensuring that each move is strategic and informed. Timely action doesn’t just lead to better results. It also provides peace of mind in an otherwise stressful situation.
Understanding Post-Judgment Collections
When a court issues a judgment, it’s a legal recognition that one party owes money to another. However, obtaining a judgment doesn’t automatically lead to payment. The real work begins with locating assets and enforcing the court’s decision. Several methods exist to aid collection, including wage garnishments, property liens, and bank levies. Each method requires understanding and expertise to execute effectively.
Why Timing Matters
Timely action impacts the recovery process in several ways:
- Preservation of Assets: Debtors may attempt to hide or transfer assets if given time.
- Legal Deadlines: Many jurisdictions impose time limits on enforcement actions. Missing these can nullify a judgment.
- Interest Accumulation: While judgments accrue interest, the longer collection takes, the less valuable the judgment becomes due to inflation and potential asset depletion.
Many experts, including those at the Department of Justice, stress the importance of not delaying enforcement actions. They provide guidelines on the legal methods available to those seeking to enforce judgments.
Strategies for Effective Post-Judgment Collection
To enhance the chances of successful recovery, it’s essential to employ strategic methods:
- Asset Investigation: Identifying the debtor’s assets is the foundation of collection.
- Legal Remedies: Use all available legal tools, from liens to garnishments, to encourage payment.
- Professional Assistance: Engaging with professionals who specialize in collections can provide advantages not readily available to individuals.
Comparing Collection Methods
The following table outlines common methods of post-judgment collection along with their benefits and potential drawbacks:
| Method | Benefits | Drawbacks |
| Wage Garnishment | Steady payment stream | Limited to a percentage of wages |
| Property Lien | Secures debt against real estate | Requires sale of property for payment |
| Bank Levy | Directly accesses debtor’s funds | One-time access; may not cover full debt |
Historical Example: Swift Action in Collections
In ancient Rome, creditors employed swift action to recover debts, often working with local magistrates to seize assets immediately. This historical precedent demonstrates the value societies have long placed on timely debt recovery. The quicker the response, the more likely a creditor would obtain due payment.
Conclusion
Timely action in post-judgment collections is not just advisable; it is essential. Acting quickly preserves legal rights and increases the likelihood of recovering owed sums. By understanding the collection process, employing strategic methods, and using historical insights, parties can enhance their recovery efforts. For more information, resources such as the Federal Reserve’s guide on money and payments provide additional insights into handling finances effectively.
-

 Home Improvement6 months ago
Home Improvement6 months agoEssential Drain Cleaning Tips for Brampton Residents
-

 Fashion11 months ago
Fashion11 months agoAttractive Beach Dresses: Elevate Your Look with These Ideas
-

 Entertainment10 months ago
Entertainment10 months agoNetnaija: Your One-Stop Shop for Free Movies in Africa
-

 Pets10 months ago
Pets10 months agoPawsitively Perfect: The Types of Dog Harness Bundle for Your Furry Friend
-

 News10 months ago
News10 months agoWhat Are the Biggest Challenges in Marine Construction Projects in Australia?
-

 Health11 months ago
Health11 months agoUnderstanding Ftmç: Gender-Affirming Surgery
-

 Business11 months ago
Business11 months agoHow Professional Concrete Cleaning Wins Repeat Business
-

 Entertainment12 months ago
Entertainment12 months agoUnlocking Cinematic Pleasures: A Comprehensive Look at Rebahin, the Free Movie Streaming Haven
















